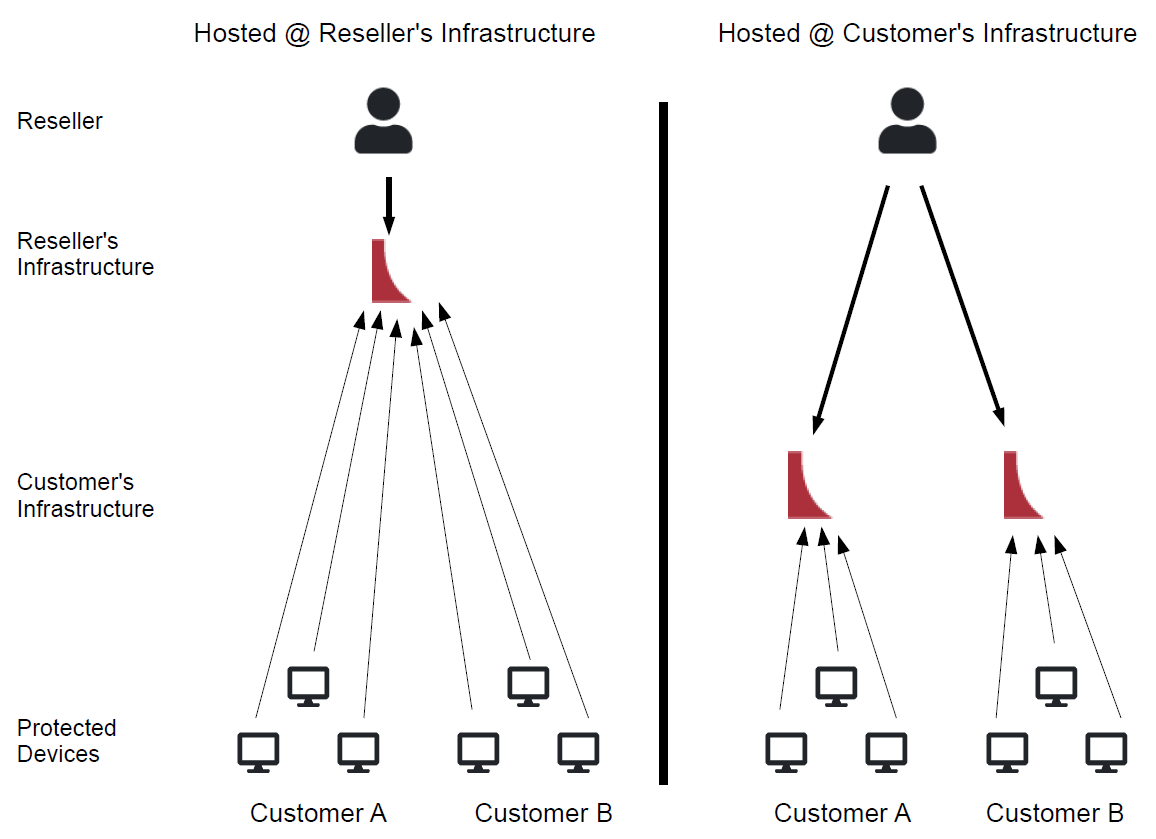
Hosting Comparison
The DCM, as an on-premise solution for TUXGUARD DEVICE SECURITY management, allows you as a reseller to host it wherever you like. There are two main scenarios for hosting:
- DCM hosted inside the infrastructure of your customer (customer in-house)
- DCM hosted inside your infrastructure (outside of the customer's infrastructure)
Both scenarios have advantages and disadvantages, outlined in the following table.
| Issue | Hosted inside Reseller's infrastructure | Hosted inside Customer's infrastructure |
|---|---|---|
| Device management of the customer | If the resellers allows, the customer is able to manage his own instances. This can be done via user & group settings. A full control over the DCM is not possible for the customer. | If the resellers allows, the customer is able to manage his own instances. This can be done via user & group settings. A full control over the DCM is possible for the customer if the admin account is handed over. |
| Device management of the reseller | Reseller can manage all instances via his own DCM. | Reseller can manage instances via accessing customer's DCM. |
| Location of usage data | Usage data is stored at Reseller's DCM. | Usage data is stored at Customer's DCM. |
| DEVICE SECURITY Updates | Instances will update themselves from Reseller's DCM. This will not save external network traffic. | Instances can update themselves from Customer's DCM. This will can save external network traffic. |
| Management of multiple customers | The reseller can manage multiple customers with only one hosted DCM | The reseller cannot manage multiple customers with only one DCM. He has to access each DCM one by one. |