TLS Certificates
During the installation process, a self-signed TLS certificate is being generated by DCM Server and placed in the following directory:
/home/ecm/tls
The relevant files are:
DCM_certificate.pem(full certificate chain file)ecm_key.key(keyfile)
Managing certificates via GUI
The certificate settings can be changed under 'System settings' --> 'Core' and by default are displaying the SHA1 fingerprint of the current certificate. The label on the left also indicates whether the autogenerated default self-signed certificate is currently used.
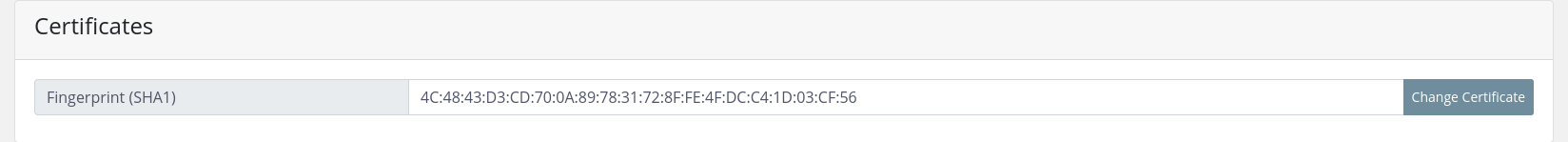
An edit menu can be accessed by clicking on the 'Change certificate' button on the right where one can upload a certificate file and the matching key file.
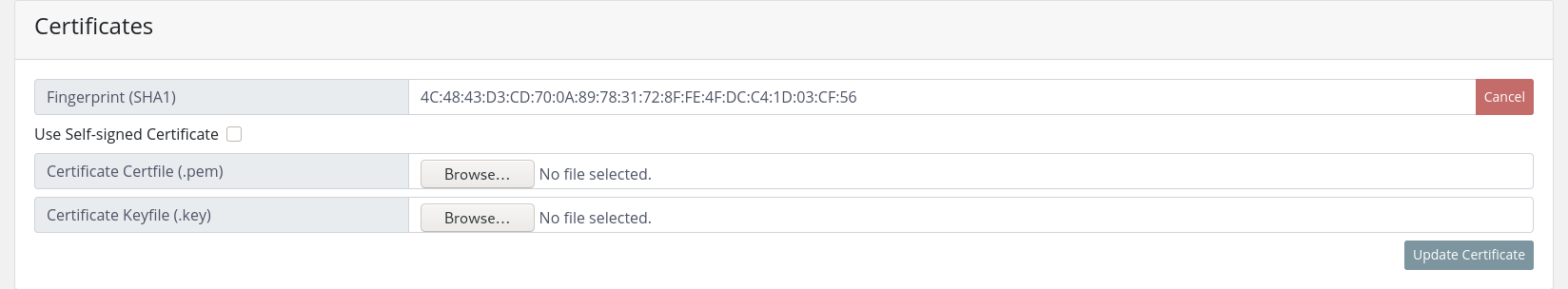
The autogenerated certificate can be activated using the 'Use self-signed Certificate' checkbox.
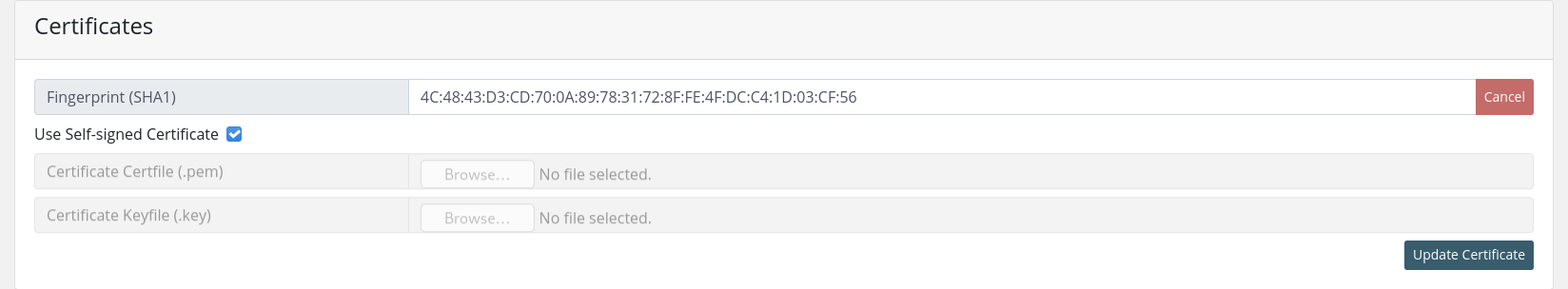
After making the desired changes, click on the 'Update Certificate' button on the bottom right to start the certificate replacement process. In case both uploaded files have been successfully verified, a message will appear and the page will be reloaded after 10 seconds.
Replacing the certificate via CLI
Currently this is only possible by connecting to your DCM Server host via SSH i.e. uploading a certificate and the matching keyfile via SCP:
scp <path_to_your_certfile.pem> root@<your_ecm_server_host_ip>:/home/ecm/ecm_certificate.pem
scp <path_to_your_keyfile.pem> root@<your_ecm_server_host_ip>:/home/ecm/ecm_key.key
Note
Your certificate file must be in .pem format and contain the following in the specified order:
- end-user certificate
- ca certificate
- intermediate certificates
After replacing the certificates it is necessary to restart the ecm-managerand 'nginx' service on your ECM Server host:
systemctl restart ecm-manager
systemctl restart nginx
Note
If you are using a self-signed certificate, please make your sure you've disabled certificate validation in the profiles you are using. Otherwise the devices are not able to retrieve updates from your DCM.